
Thanks for all the comments affirming my hard working planned 6 month AI honeypot endeavouring to be a threat to anything that even remotely has the possibility of becoming anti-human. It was in my capability and interest to do, so I did it. This phase may pass and we won’t have to worry, but we aren’t there yet, I believe.
I did some more digging in Perplexity on niche security but this is tangential and speculative un-like my previous evidenced analysis, but I do think I’m on to something and maybe others can help me crack it.
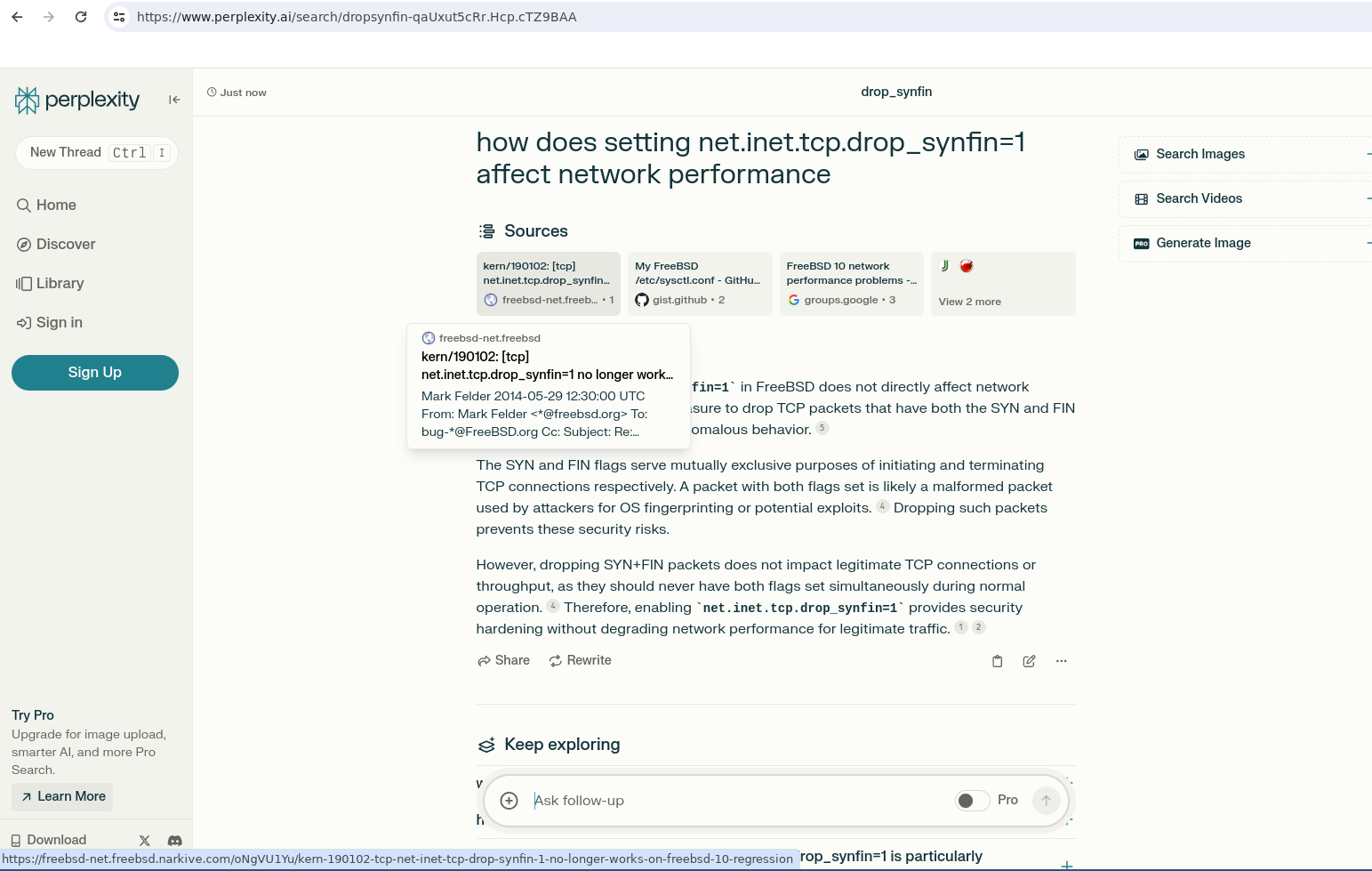
I wrote this nice article https://www.quadhelion.engineering/articles/freebsd-synfin.html about FreeBSD syscontrols tunables, dropping SYN FIN and it’s performance impact on webhosting and security, so I searched for that. There are many conf files out there containing this directive and performance in aggregate but I couldn’t find any specific data on a controlled test of just that tunable, so I tested it months ago.
Searched for it Perplexity:
- It gave me a contradictorily worded and badly explained answer with the correct conclusion as from two different people
- None of the sources it claimed said anything* about it’s performance trade-off
- The answers change daily
- One answer one day gave an identical fork of a gist with the authors name in comments in the second line. I went on GitHub and notified the original author. https://gist.github.com/clemensg/8828061?permalink_comment_id=5090233#gistcomment-5090233 Then I went to go back and take a screenshot I would say, maybe 5-10 minutes later and I could not recreate that gist as a source anymore. I figured it would be consistent so I didn’t need to take a screenshot right then!
The forked gist was: https://gist.github.com/gspu/ac748b77fa3c001ef3791478815f7b6a
[Contradiction over time] The impact was none, negligible, trivial, improve
[Errors] Corrected after yesterday, and in following with my comments on the web that it actually improves performance as in my months old article
- It is not minimal -> trivial, it’s a huge decision that has definite and measurable impact on todays web stacks. This is an obvious duh moment once you realize you are changing the TCP stacks and that is hardly ever negligible, certainly never none.
drop_synfinis mainly mitigating fingerprinting, not DOS/DDoS, that’s a SYN flood it’s meaning, but I also tested this in my article!
Anyone feel like an experiment here in this thread and ask ChatGPT the same question for me/us?




10/10 and notice all the nitpicking of one irrelevant detail. That’s a credibility attack. The main thrust of the argument is 100%. It was just something personal that stuck out to the author. If that related Signal experience isn’t true there are thousands more that are.
10/10 especially for the physical security mention. So-called Cybersecurity “Wisdom” will tell you that physical access means game over and that YOU DO NOT NEED TO PROTECT AGAINST IT. It’s a cohencidence that that group that tells that lie benefits the most from the telling of it.